Information Assurance Standard V1, March 2021
Return to Evidence of Identity Standard
This information is an archival record and is retained for reference purposes only.
You can access the latest version at Information Assurance Standard – digital.govt.nz
This standard provides specific information management controls to ensure information collected is suitable for accurate decisions to be made regarding the eligibility or capability of an Entity.
Application of this standard
This standard applies to any Relying Party (RP). The RP is accountable for the controls stated in this standard, even if they have employed or contracted aspects to other parties.
Application of the controls in this standard will contribute to the reduction of identity theft, entitlement fraud, misrepresentation of abilities and the impacts that result.
Effective date
This standard is effective from 1 March 2021.
It replaces the requirements outlined in Table 8 of the Evidence of Identity Standard (EOI) Standard version 2.0 — Dec 2009 relating to Objective A — Identity exists.
Scope
This standard applies whenever information related to an entity is collected and stored (whether during enrolment or a subsequent transaction).
Effective information and records management ensures the creation, usability, maintenance, and sustainability of the information and records needed for business operations.
Requirements for good practice information management come from many sources including, but not limited to, the Privacy Act 1993 (currently under review) and the Public Records Act 2005.
This standard does not replace these requirements but provides requirements for Identification Management, in the form of controls that are not explicit elsewhere.
In relation to the scope of Identification management, this standard relates to the quality of ‘entity information’, as indicated in the diagram below.
Diagram 1: Relationship between elements
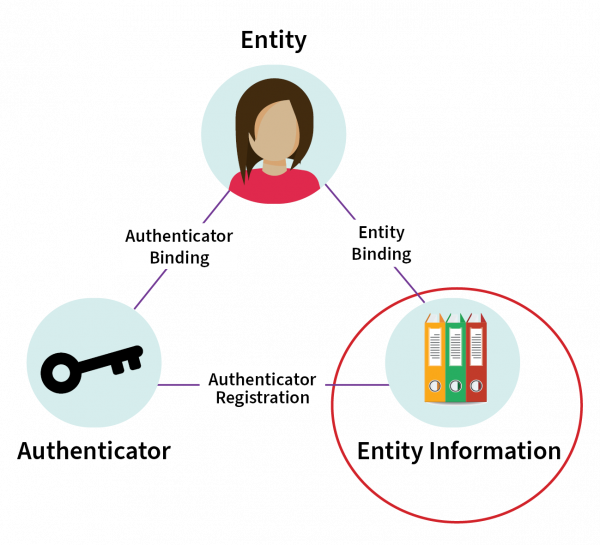
Detailed description of the image
A diagram shows a triangle representing the connection between Entity (in this example, represented by a person) at the top of the triangle, Authenticator (represented by a key) at the bottom left, and Entity Information (represented by files of information) at the bottom right.
The connection between Entity and Entity Information is labelled Entity Binding, the connection between Entity Information and Authenticator is labelled Authenticator Registration and connection between Authenticator and Entity is Authenticator Binding.
There is a red circle around Entity information to indicate the scope of this standard’s content in relation to other elements.
Relationship with other identification management standards
Assurance components
Table 1 describes each of the assurance components and the processes they relate to. This standard addresses the first of these assurance components — Information Assurance (IA).
| Assurance component | Description |
|---|---|
|
IA Information Assurance |
Robustness of the process to establish the quality and accuracy of Entity Information. |
|
BA Binding Assurance |
Robustness of the process to bind the Entity to Entity Information and/or Entity to Authenticator. |
|
AA Authentication Assurance |
Robustness of the process to ensure an Authenticator remains solely in control of its holder. |
|
FA Federation Assurance |
Additional steps undertaken to maintain the integrity, security and privacy of a credential used in many contexts. |
Requirements
Objective 1 — Information risk is understood
Rationale
For entities to trust that their information is sought and used appropriately, the information assurance (IA) level should be consistent with the risk posed.
Relying parties may also need to achieve specific levels of assurance to mitigate risks and potentially to comply with legislation.
IA1.01 Control
The RP MUST carry out an assessment of the information risk posed by any service before offering it.
Additional information – While any risk assessment process can be used, specific guidance is available on assessing identification risk.
Objective 2 — Information is protected
Rationale
A key part of preventing identity theft is to build protections into the collection and storage of information from the beginning.
IA2.01 Control
The RP MUST collect enough distinctive information, related to an entity, for it to be distinguishable from another entity’s information.
Additional information — Otherwise known as Entity information uniqueness. Entity information is likely to be made unique by an internal system number and by the addition of any reference identifier. However, this will be insufficient if these are not known by the claiming entity. The lack of distinctive information will also make it difficult to identify potential fraud where 2 entities attempt to claim the same entity information.
IA2.02 Control
The RP MUST have a justifiable need for every piece of information it collects.
IA2.03 Control
The RP MUST store only the information it requires to carry out its purpose.
Additional information — This includes considering if the full value of a piece of information is needed, a derived value from the information or a reference to some source of the information.
IA2.04 Control
Where information is collected for the sole purpose of verifying required information, the RP MUST discard this information once verification is complete.
Additional information — Under this requirement, the RP may keep a record that the information was collected, and the verification process undertaken – See IA4.04.
Objective 3 — Information is accurate
Rationale
The quality of the information being sought is key to its usefulness for decision making or administrative needs.
The level of assurance needed for information is established through undertaking a suitable risk assessment process.
IA3.01 Control
The RP SHOULD use recommended data format standards for collection and storage of information.
IA3.02 Control
The RP MUST establish the level of information assurance (IA) required, for each piece of information collected.
Additional information — The outcome of the risk assessment can be used to determine the level of assurance.
IA3.03 Control
The RP selects suitable evidence, that matches the level of information assurance (IA) required for verifying each piece of information.
For level 1 – The RP SHOULD use the entity as the evidence.
For level 2 – The RP SHOULD select evidence that has at least referenced a copy of an authoritative source as part of their creation.
For level 3 – The RP MUST select evidence that is a copy of an authoritative source, at a minimum.
For level 4 – The RP MUST select evidence that is an authoritative source or has a continuously synchronised link to an authoritative source, such that they are considered equal.
IA3.04 Control
The RP MUST verify each piece of information against its selected evidence.
IA3.05 Control
The RP MUST NOT assign a level of assurance to evidence whose level has not been declared.
Objective 4 — Quality of evidence
Rationale
The level of accuracy of information is also dependent on the trustworthiness of the evidence used. Whether the evidence is a physical document, electronic credential or database the RP needs to have some assurance that the evidence is genuine.
IA4.01 Control
The RP establishes the quality of the evidence is consistent with the level of information assurance (IA) required.
For level 1 – The RP MUST accept the entity as the evidence
For level 2 – The RP MUST take the evidence at ‘face value’.
For level 3 – The RP MUST base quality on the evidence being manually identified and/or include physical security features that require proprietary knowledge to be able to reproduce it.
For level 4 – The RP MUST base quality on the evidence being systematically identified and accessed through a trusted communication channel.
IA4.02 Control
The RP establishes if any evidence has a registered status (such as suspended or revoked), that makes it unusable.
For level 1 and 2 – The control does not apply
For level 3 – The RP SHOULD check for registered statuses with evidence issuers or equivalent service providers.
For level 4 – The RP MUST check for registered statuses with evidence issuers or equivalent service providers.
IA4.03 Control
The RP applies counter-fraud techniques, where possible.
For level 1 and 2 – The control does not apply
For level 3 – The RP SHOULD apply counter-fraud techniques.
For level 4 – The RP MUST apply counter-fraud techniques.
Additional information – More information is available in the guide Counter-fraud techniques.
IA4.04 Control
The RP MUST store appropriate detail about the information verification and evidence to enable queries or investigation in the future.
What compliance means
In order to comply with this standard ALL the controls will be met at the level required.
Voluntary compliance by any RP wishing to follow good practice for contributing to the prevention of identity theft and fraud, will be against the levels indicated by undertaking a risk assessment.
Compliance with this Standard given through means such as contractual requirements, cabinet mandate, legislation etc., will include mechanisms for assessment and certification. The RP will meet the levels determined by the risk assessment and any additional requirements specified.
Related advice
If the RP is providing information assurance services to other parties, there will be additional controls to be applied in the Federation Assurance Standard.
For additional guidance on implementing the controls in this standard refer to Implementing the Information Assurance Standard.
Contact
Department of Internal Affairs Te Tari Taiwhenua